
Tata Consultancy Services (TCS) denied reports that it lost a $1 billion contract with Marks & Spencer (M&S) due to a cyberattack.
The company called the report “misleading”, saying M&S chose to work with other partners well before the April 2025 cyber incident.
TCS added that the report contained factual inaccuracies regarding the contract’s size and its ongoing work with M&S.
Tata Consultancy Services (TCS) on Monday dismissed reports claiming that the Indian IT giant lost a $1 billion contract from British retailer Marks and Spencer (M&S). The reports had claimed that the loss was due to a cyberattack M&S faced earlier this year.
The Tata group company called the report "misleading", claiming that the retailer decided to work with other partners "much prior to the cyber incident in April 2025", and that the two matters are "clearly unrelated."
"The report published by The Telegraph is misleading, with factual inaccuracies including the size of the contract and the continuity of TCS’ work for Marks & Spencer (M&S)," the firm said in an exchange filing on October 27.
Although this contract was not cancelled due to the cyberattack incident, it did hurt TCS' overall business in the last quarter. Before we get into that, let’s try to understand what happened with M&S.
Cyberattack on M&S
In late April this year, stores of Marks & Spencer came under attack from a hacker group called Scattered Spider (also known as Octo Tempest). They reportedly used phishing, credential theft, and deployed the ransomware DragonForce to encrypt key systems.
The attack led the retailer to shut down its in-store pickup purchases and M&S' contactless payment system.
The attack was part of a series of sophisticated attacks on UK retailers earlier this year, which also impacted luxury department store Harrods and supermarket chain Co-op.
Later that month, M&S, in its annual report, said it estimated a £300 million hit to profits this year. Marks & Spencer chief executive Stuart Machin said hackers gained access to the retailer’s systems through one of its contractors by using "social engineering" techniques — methods that often involve impersonating employees to deceive helpdesk staff. He emphasised that the breach did not stem from any weakness in M&S’ own IT systems but occurred via a third-party vendor.
Machin added that the company expects to recover swiftly from the disruption, with its website likely to reopen within the next few weeks and full sales operations resuming across all product categories before July.
At the time, local media reports speculated that this compromised third-party contractor was Tata Consultancy Services (TCS), which manages M&S’s helpdesk among other IT services.
Though TCS denied any mishap from their part, the company said the breach occurred “in the client’s own environment” and that it had found “no indicators of compromise within the TCS network.”
It’s worth noting that Tata Consultancy Services (TCS) has been Marks & Spencer’s (M&S) principal technology partner since 2018, when the UK retailer began its five-year digital transformation programme. The partnership was extended in 2023. At the time, it was noted that the extended deal would focus on modernising M&S’s core business systems, including cloud adoption, supply chain efficiency, and omnichannel capabilities. While neither company has disclosed the contract’s exact value, media reports have estimated it at around $1 billion.
The above-mentioned contract, both parties have publicly confirmed, continues.
The Lost Contract
According to TCS, the contract M&S has taken from the IT giant relates to “service desk” work. Tata Group's IT arm won this contract via a competitive bid. In January, the UK retailer didn’t opt to renew these services and went to the market to find a different partner.
“The commercial aspect of the service desk area also represents an insignificant part of TCS’ overall engagement with M&S,” TCS told investors in its exchange filing today.
However, its second-quarter earnings report tells a different story.
In the quarter ending September 30, 2025, the IT giant lost two clients in the mega-deal category. According to its Q2 FY26 investor presentation, in the higher-value client brackets (contracts worth over $100 million), TCS’s total clients fell from 62 in Q1 FY26 to 60 in Q2 FY26, though the rest of the categories saw additions.
JM Financial analysts covering the Mumbai-based firm noted that “new projects stalled due to a cyberattack at a key client are expected to ramp.”
But TCS CEO K Krithivasan told analysts in the post-earnings conference call that “macros have not changed much,” but the number of projects getting deferred or paused has reduced compared to the preceding quarter.
He said that clients continued to keep tight control over discretionary budgets, focusing on vendor consolidation to achieve transformation objectives. He added that while smaller deals did not see any significant improvement, they witnessed an increase in the number of rapid-build and modernisation projects.
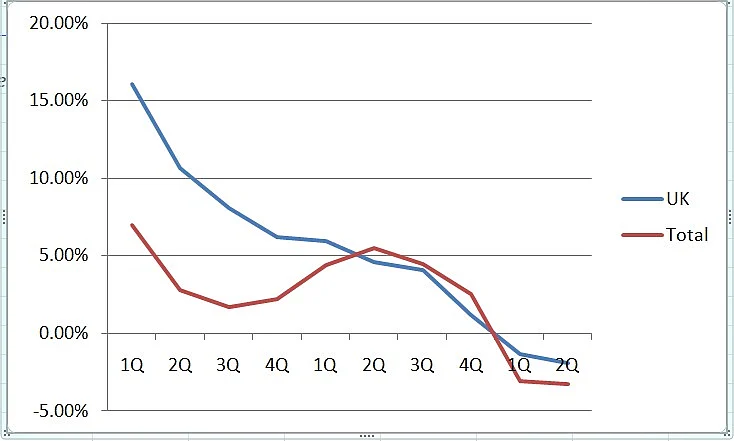
Notably, in Q2, TCS’s revenue growth was weak across geographies except in the UK. According to research noted by INDSEC, in Q2, amongst geographies, MEA and India showed strong growth momentum with 5.9% and 4% quarter-on-quarter constant currency growth, while Continental Europe and North America returned to positive sequential growth with 1.4% and 0.8% growth respectively. But the UK reported negative 1.4% QoQ CC growth.
The region hasn’t been doing well for the company in past quarters either. After seeing double-digit growth in FY24, the company’s sequential revenue growth in the UK has been dropping. In Q1 FY25 it saw revenue growth of 6%, which continued to slow since then. In Q1 FY26 it had turned negative at 1.3%, which further extended this quarter.
To be sure, overall TCS hasn't grew much since FY24, but the decline in UK has been much sharper.
Cyberattack Pressure on Indian IT Firms
Following the M&S attack, TCS faced another blow in early September 2025 as JLR, the UK-based luxury automaker, was hit by a major cyberattack. The attack forced the temporary shutdown of its UK factories. Under a five-year, approximately £800 million contract signed in 2023, TCS had been responsible for managing large parts of JLR’s IT infrastructure and cybersecurity operations. Though there are no official comments on whether TCS was responsible for the attack, it has come under scrutiny by the UK Parliament’s Business & Trade Committee.
The committee has demanded detailed information about its services, scope of involvement, and any investigations into the incident.
In its Q2 earning conference, TCS addressed the recent cybersecurity incidents, clarifying that TCS systems were not impacted and that client projects affected by the event are expected to pick up in the coming weeks.
TCS is not alone. In July 2025, Clorox filed a lawsuit against Cognizant seeking $380 million in damages, alleging gross negligence by the IT services firm in connection with a cyberattack on Clorox in August 2023. Clorox claims that a hacker posed as an employee, phoned Cognizant’s service desk, and obtained network credentials without proper verification, allowing access to its systems and resulting in widespread operational disruption, including manufacturing halts and lost revenue.
Cognizant, for its part, says its role was limited to helpdesk services and claims Clorox’s own internal cybersecurity arrangements were deficient.
But these attacks have hurt the reputations of Indian IT giants. HFS Research’s Phil Fersht and Akshat Tyagi wrote in May that for every cyberattack that goes public, they estimate another six are kept under wraps “to avoid negative publicity.”
“The pressure point has become the CIO, who not only has to manage significant pressures from their boards and leadership peers to deliver an AI agenda, but they also have to balance this with a proactive, holistic cybersecurity approach that business leaders can comprehend. Mess up your cybersecurity, and you’re not only fired, but your entire firm may just sink with you,” they wrote.



































